SECURITY OPERATIONS CENTRE (SOC) SOLUTIONS
Comprehensive SOC Solutions for Real-Time Threat Detection, Response, and Compliance – All in One Platform.
We’re here to answer any question you may have.
Would you like to join our growing team?
careers@hub.com
Would you like to join our growing team?
careers@hub.com
Error: Contact form not found.
Comprehensive SOC Solutions for Real-Time Threat Detection, Response, and Compliance – All in One Platform.




















CyberDisti, a cybersecurity distributor empowering digital resilience across the GCC, is proud to bring cutting-edge Security Operations Center (SOC) Services through its partnership with Seceon, a globally trusted platform for unified threat management and response.
Our SOC offering is purpose-built for enterprises seeking real-time security intelligence, seamless automation, and rapid response to evolving threats. Delivered as an in-house or hybrid model, our solution helps you:
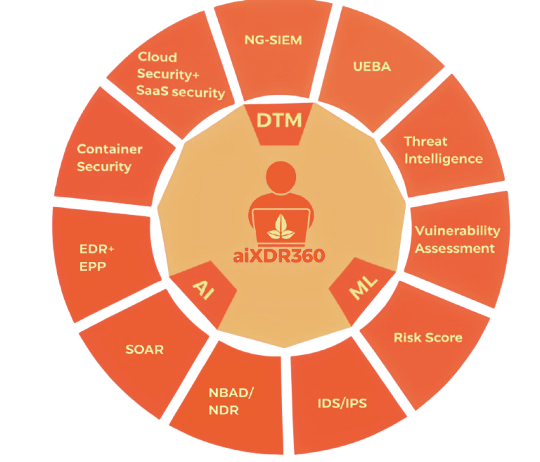
With seamless integration of logs, user behavior, endpoint telemetry, cloud, application, and network data — CyberDisti’s SOC platform delivers:
🔁 Continuous Monitoring
🤖 AI/ML-Based Threat Correlation
📊 Security Posture Visualization
🛡️ Automated Policy Enforcement
📁 Intelligent Log Retention & Search
🔄 Unified Security Operations in one platform
⚡ Rapid Deployment with minimal infrastructure overhead
🌍 Scalable Architecture for small to large enterprises
🧠 Smart Automation for reduced manual intervention
💼 Trusted Across Industries – BFSI, healthcare, retail, and more
Our Features and Benefits



Adding {{itemName}} to cart
Added {{itemName}} to cart