
Purpose Built for Zero Trust to Protect Organizations from Breaches and Data Loss
The iboss Zero Trust Edge prevents breaches by making applications, data and services inaccessible to attackers while allowing trusted users to securely and directly connect to protected resources from anywhere
Unrivaled Global Cloud Network Security Fabric.
A containerized architecture built for infinite scalability. iboss created and operates one of the largest global cloud network security fabrics on earth. A scalable global service ensures Zero Trust network security and peace of mind, regardless of where users work.
150B+ Transactions Daily
The iboss Cloud Platform secures 150B+ transactions per day
100+ Global POPs
One of the largest SASE platforms with over 100+ Points of Presence.
4B+ Threats Prevented Daily
On average, we are preventing over 4B+ security threats per day.
150+ Countries Connected
Places access closer to users giving faster secure connections anywhere.
iboss Zero Trust Edge
Purpose Built for Zero Trust to Protect Organizations from Breaches and Data Loss
The iboss Zero Trust Edge prevents breaches by making applications, data and services inaccessible to attackers while allowing trusted users to securely and directly connect to protected resources from anywhere
iboss Makes ALL Resources Private
Properly implementing Zero Trust involves ensuring that protected applications, data and services cannot be accessed without going through the Zero Trust security edge.
IPv6 Support to Ensure Users Can Connect from Anywhere
IPv6 is quickly becoming the dominant connection protocol used globally as the IPv4 address space is completely exhausted. Unlike competitors that do not support IPv6 through the proxy Policy Enforcement Points, the iboss Zero Trust Edge completely supports IPv6 throughout the service to ensure users can connect from any location and through any Internet provider.
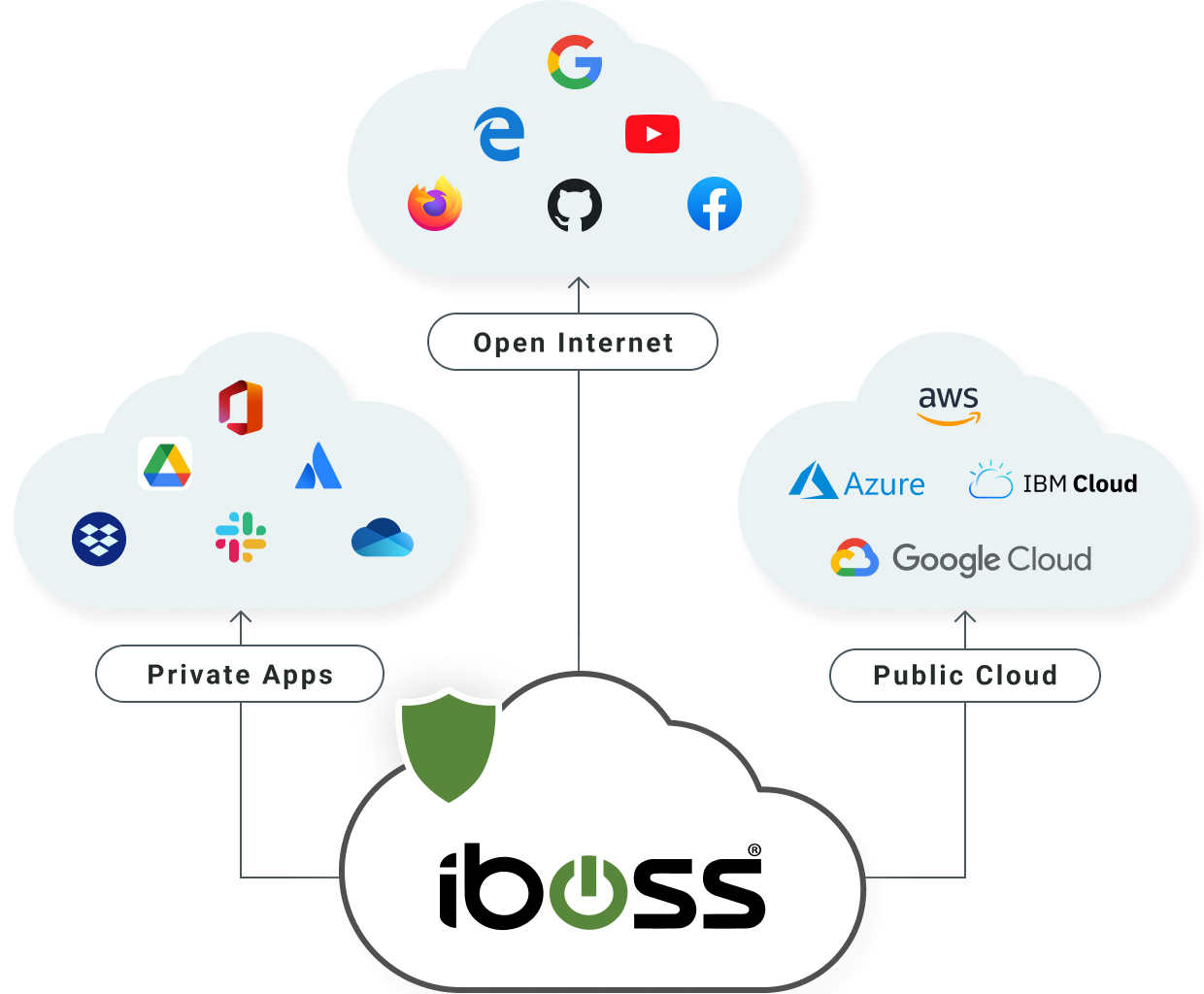
A Single Unified Global Zero Trust Edge Ensures Consistent Visibility and Protection
Unlike legacy cloud competitors which separate “Private Access” from “Internet Access”, iboss uses a single Zero Trust Edge to protect all resources equally regardless of whether they are on-prem or in the cloud. With iboss, ALL resources are Private, meaning applications, data and services owned and protected by the organization are NEVER accessible without being authorized by the iboss Zero Trust Edge.
Trust Algorithms and Trust Scoring Prevent Breaches and Data Loss
The NIST 800-207 Zero Trust Architecture Publication outlines Trust Algorithms which are needed to increase decision confidence when the Zero Trust service grants or denies access to a protected resource. The iboss platform provides criteria-based and score-based algorithms to ensure thePolicy Enforcement Points make adaptive and intelligent decisions when granting or denying access to protected resources.
An Elastic Zero Trust Edge Ensures Seamless Hybrid Protection
The iboss Zero Trust Edge uses a containerized edge which allows the data plane of the service to extend on-prem into the customer data center. This is an extension of the global security edge and allows protection of on-prem resources with the same CASB, Malware Defense and Data Loss Prevention capabilities even though those transaction may traverse private cloud Policy Enforcement Points.
